Best Of The Best Info About How To Detect Gh0st Rat

[2] it is a cyber spying computer program.
How to detect gh0st rat. Some threats reinstall themselves if you don't delete their core files. Whenever you browse something by using your default browser. There are a large number of remote access trojans.
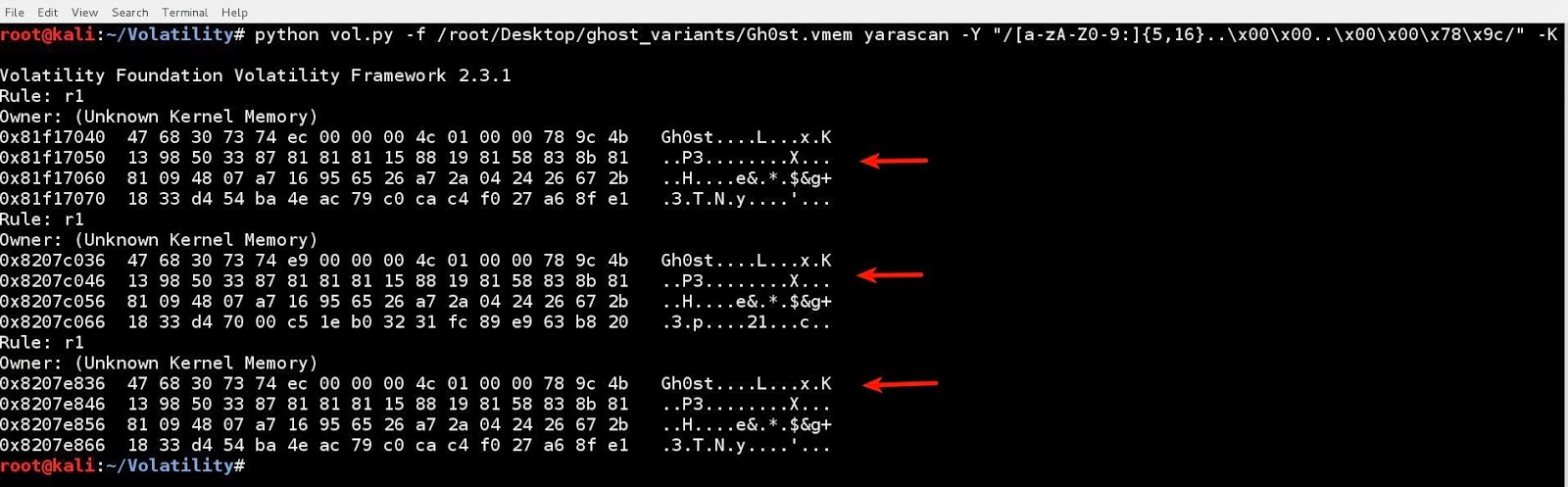
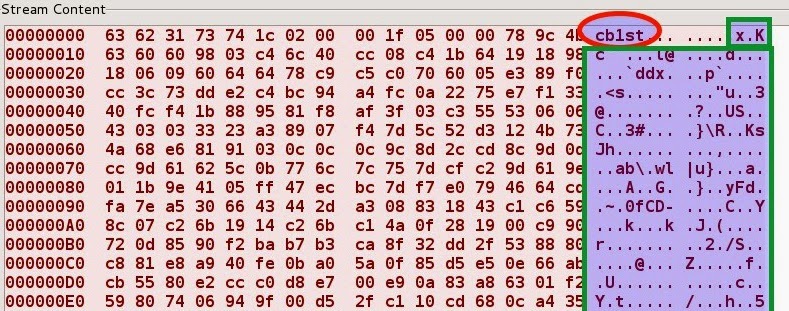
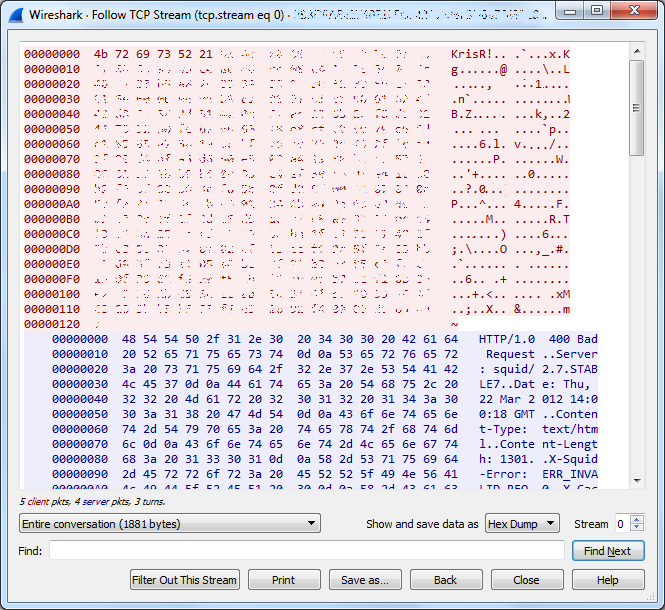
This indicates that a system might be infected by the gh0st rat botnet. The gh0st rat is often active in campaigns targeting. Below is the packet information that is exchanged between a ghost rat client and a compromised host.
There are 10 signs from which any users can get that their pc is infected by some virus/malware like gh0st rat. Gh0st rat is a windows malware that can remotely control a computer to log key strokes, take. For an efficient gh0stcringe rat detection, use the sigma rule below developed by the talented member of soc prime threat bounty program sittikorn sangrattanapitak, to.
The dropper executable is then launched and it decrypts and. This commit does not belong to any branch. The gh0st rat is a remote access trojan that can give the cybercrooks the ability to access and control your pc remotely.
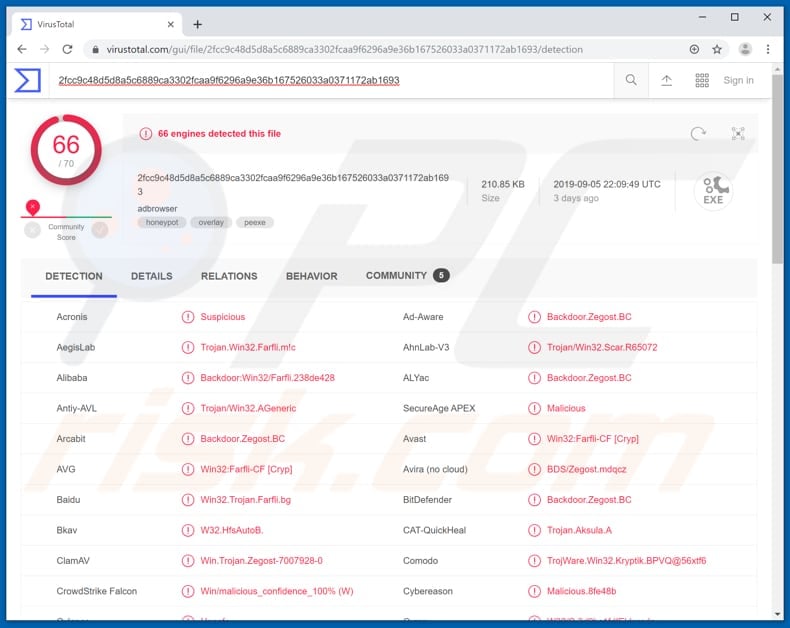
So, if no av in the world classifies this as gh0st, it’s probably not. According to security ninja, gh0st rat (remote access terminal) is a trojan “remote access tool” used on windows platforms, and has been used to hack into some of the most sensitive. For media inquiries, please contact [email protected].
Scan your computer for threats with spyhunter. Address 4501 north fairfax dr., suite 710 arlington, va 22203. We recommend downloading spyhunter to remove harmful.









_(1)_(1).jpg)